Выдержки из Chapter 3 книги Cisco Press "Interconnecting Cisco Network Devices, Part 1 (ICND1): CCNA Exam 640-802 and ICND1 Exam 640-822" для повторения перед экзаменом.
ITU-R Local FCC Wireless
Three unlicensed bands exist: 900 MHz, 2.4 GHz, and 5.7 GHz. The 900-MHz and 2.4-GHz bands are referred to as the ISM bands, and the 5-GHz band is commonly referred to as the Unlicensed National Information Infrastructure (UNII) band.
Frequencies for these bands are as follows:
· 900-MHz band: 902 MHz to 928 MHz.
· 2.4-GHz band: 2.400 GHz to 2.483 GHz (in Japan, this band extends to 2.495 GHz.)
· 5-GHz band: 5.150 GHz to 5.350 GHz, 5.725 GHz to 5.825 GHz, with some countries supporting middle bands between 5.350 GHz and 5.725 GHz. Not all countries permit IEEE 802.11a, and the available spectrum varies widely. The list of countries that permit 802.11a is changing.
802.11 Standards
Summary of Exploring Wireless Networking
The following summarizes the key points that were discussed in this section:
· People now expect to be connected at any time at any place. However, the most tangible benefit of wireless is cost reduction.
· Both WLANs and LANS use CSMA. However, WLANs use CA, whereas LANs used CD.
· Radio frequencies are radiated into the air by antennas where they are affected by:
Reflection
Scattering
Absorption
· The IEEE defines the 802.11 standards.
· The ITU-R local FCC wireless bands are unlicensed.
· The 802.11 standards are a set of standards that define the frequencies and radio bands for WLANs.
· One of the primary benefits of the Wi-Fi Alliance is to ensure interoperability among 802.11 products.
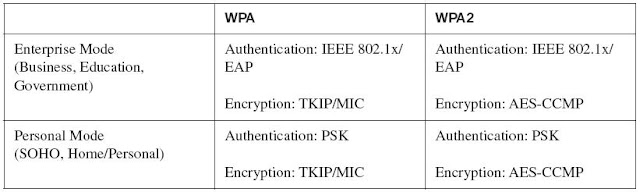
WPA Modes
Enterprise Mode is a term given to products that are tested to be interoperable in both PSK and 802.1x/Extensible Authentication Protocol (EAP) modes of operation for authentication. Personal Mode
Personal Mode is a term given to products tested to be interoperable in the PSK-only mode of operation for authentication. It requires manual configuration of a preshared key on the AP and clients. PSK authenticates users via a password, or identifying code, on both the client station and the AP. No authentication server is needed. Personal Mode is targeted to SOHO environments.
Summary of Understanding WLAN Security
The following summarizes the key points that were discussed in this lesson:
· With 802.1x, the access point, acting as the authenticator at the enterprise edge, allows the client to associate using open authentication.
· WPA provides authentication support via IEEE 802.1x and PSK.
Enterprise Mode is a term given to products that are tested to be interoperable in both PSK and IEEE 802.1x/EAP modes of operation for authentication.
Personal Mode is a term given to products tested to be interoperable in the PSK-only mode of operation for authentication.
802.11 Topology Building Blocks
· Ad hoc mode: Independent Basic Service Set (IBSS) is the ad hoc topology mode.
Mobile clients connect directly without an intermediate access point. Operating systems such as Windows have made this peer-to-peer network easy to set up. This setup can be used for a small office (or home office) to allow a laptop to be connected to the main PC or for several people to simply share files. The coverage is limited. Everyone must be able to hear everyone else. An access point is not required. A drawback of peer-to-peer networks is that they are difficult to secure.
· Infrastructure mode: In infrastructure mode, clients connect through an access point. There are two infrastructure modes:
Basic Service Set (BSS): The communication devices that create a BSS are mobile clients using a single access point to connect to each other or to wired network resources. The Basic Service Set Identifier (BSSID) is the Layer 2 MAC address of the BSS access point’s radio card. While the BSS is the single building block for wireless topology and the BSS access point is uniquely identified through a BSSID, the wireless network itself is advertised through a SSID, which announces the availability of the wireless network to mobile clients. The SSID is a wireless network name that is user configurable and can be made up of as many as 32 case-sensitive characters.
Extended Services Set (ESS): The wireless topology is extended with two or more BSSs connected by a distribution system (DS) or a wired infrastructure. An ESS generally includes a common SSID to allow roaming from access point to access point without requiring client configuration.
The characteristics of data rates as they apply to client devices and signal strength:
· Higher data rates require stronger signals at the receiver. Therefore, lower data rates have a greater range.
· Wireless clients always try to communicate with the highest possible data rate.
· The client reduces the data rate only if transmission errors and transmission retries occur.
Steps to Implement a Wireless Network
The basic approach to wireless implementation (as with any basic networking) is to gradually configure and test incrementally, following these steps:
Step 1 Before implementing any wireless, verify pre-existing network and Internet access for the wired hosts.
Step 2 Implement wireless with only a single access point and a single client, without wireless security.
Step 3 Verify that the wireless client has received a DHCP IP address and can ping the local wired default router and then browse to the external Internet.
Step 4 Finally, configure wireless security with WPA/WPA2. Only use WEP if hardware equipment does not support WPA/WPA2.
Summary of Implementing a WLAN
The following summarizes the key points that were discussed in this lesson:
· Ad hoc mode: Clients connect directly without an intermediate access point.
· Infrastructure mode: Clients connect through an access point. There are two modes:
Basic Service Set (BSS)
Extended Services Set (ESS)
· BSS wireless topology:
Basic Service Area (BSA)
Extended Service Area (ESA)
· Wireless access points can be configured through a command-line interface or more commonly a browser GUI.
· The basic approach to wireless implementation is to gradually configure and test incrementally.
· Currently, many form factors exist to add wireless to existing laptops:
Windows Zero Configuration
Cisco Compatible Extensions
Cisco Secure Services Client
· Troubleshooting wireless by breaking the environment into wired network versus wireless network.
Chapter Summary
The different 802.11 standards identify the characters of the transmissions used WLANs, while the Wi-Fi certification ensures compatibility between devices.
To address common threats to WLAN services, security has evolved to include WPA/WPA2.
Wireless implementations are affected by distance, speed, and form factors.


Комментариев нет:
Отправить комментарий